Introduction
Wireshark is one of the most powerful and widely-used network protocol analyzers. It allows you to capture and interactively browse the traffic running on a computer network. Whether you’re a network administrator, cybersecurity professional, or just someone interested in learning more about how networks operate, Wireshark is an invaluable tool. This blog will guide you through the basics of using Wireshark, helping you to get started with capturing and analyzing network traffic.
Why Use Wireshark?
Wireshark is indispensable for several reasons:
- Network Troubleshooting: Identify bottlenecks, diagnose slowdowns, and pinpoint causes of packet loss or high latency.
- Security Analysis: Detect abnormal traffic patterns, potential intrusions, or data exfiltration attempsts.
- Protocol Understanding: Dive deep into how different network protocols function, helping you understand the intricacies of network.
- Learning Tool: Gain hands on experience by observing real time network traffic, making abatract networking concepts tangible.
Installing Wireshark
- Windows: Download the installer from the Wireshark website and follow the setup wizard.
-
mac OS: Install it via Homebew using
brew install wiresharkor download it directly. -
Linux: Use your distribitution's package manager, e.g.,
sudo apt-get install wiresharkfor debian base systems.
Understanding the interface
Upon launching wireshark, you are greeted with a somewhat intimidating interface. Here is a breakdown to get us comfirtable with:
Capturing Traffic
To start capturing traffic, follow these steps:
- Select an interface: Choose the netwok interface through which the traffic you want to capture is passing. This could be your Ethernet, wi-Fi, or even a loopback adapater.
-
Start Capture: Click the shark fin icon

Capture > Startto start capturing the data. -
Stop Capture: Click the red square

Capture > Stopwhen you have captured enough data.
Filtering Traffic : Narrowing Down the Data
Wireshark's filtering capabilities are one of its most powerful features. Here are some common filters:
-
Filter by ip address:
ip.addr == 192.168.1.1To show all traffic to or from a specific IP address. -
Filter by Protocol:
http, tcp, udp, dnsTo focus on specific protocols. -
Filter by Port:
tcp.port == 80To filter traffic based on a specific port number. -
Exclude Traffic:
!ip.addr == 192.168.1.1To exclude a specific IP address from the results.
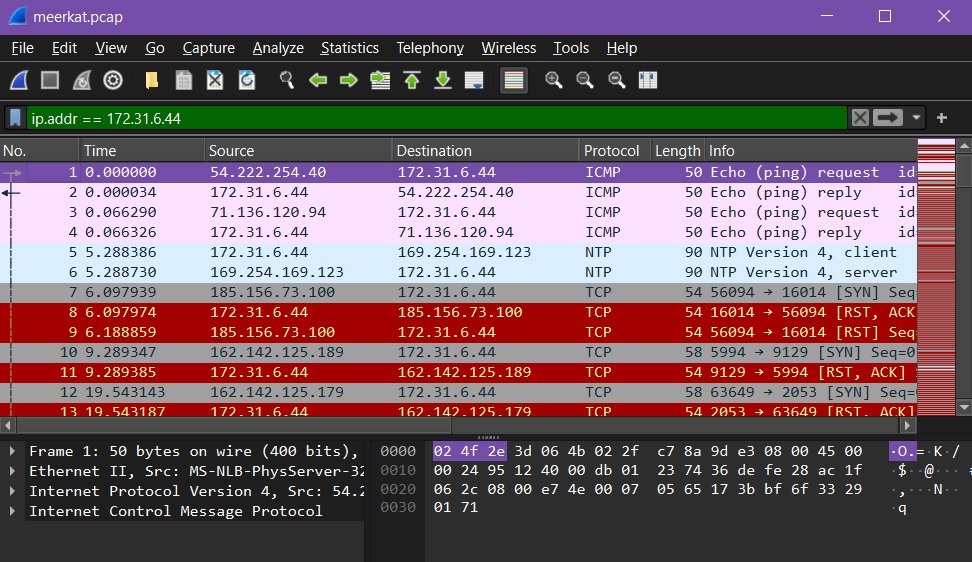
You can also combine filters for more refined searches. For example,
ip.addr == 192.168.1.1 && tcp.port == 443 show only the HTTPS traffic to or from a
specific IP.
Analyzing Captured Data
Once you have captured and filtered the traffic, you can start analyzing the packet in details:
- Follow a TCP Stream: To see the entire conversation between a client and a server, right-click on a TCP packet and select follow > TCP Stream. This feature is particularly useful for understandign how data flows in a connection.
- Inspect Packet Details: By clicking on any packet in the Packet List Pane, you can expand different layers (ethernet, IP, TCP, etc.) in the PacketDetails Pane to see headers and data paylods.
- Export Data: Save the captured traffic as a .pcap file for future analysis or for sharing the file with collegues.
Advanced Features
Once you're comfortable with the basics, you can explore some of Wireshark's advanced features:
- Custom Filters: Create custom display filters that fit your specific analysis needs.
- Color Coding: Use color rules to visually distinguish different types of traffic, making it easier to spot anomalies.
- Expert Information: Wireshark's Expert Information tool flags potential issues like malformed packets or protocol violations, giving you a heads-up on what might be wrong.
- Statistics and Graphs: Utilize built-in tools to generate traffic graphs, protocol hierarchies, and conversations. This data visualization can help you understand network behavior over time.
Conclusion
Wireshark is a powerful tool that offers both depth and flexibility in network analysis. By
starting with simple captures and gradually exploring more complex scenarios, you can unlock its
full potential. Whether you're troubleshooting a slow network, securing your infrastructure, or
simply learning more about how networks operate, Wireshark will be your go-to tool.
As you continue to practice and explore its features, you'll gain the skills needed to tackle
even the most complex networking challenges. Happy capturing!
Feel free to leave any questions or feedback in the comments below.